#BYTECATRAZ SecuRing CTF 2024
The competition, named BYTECATRAZ, took participants into the world of prison challenges. The players’ main goal was to escape from prison, helped by their cellmate Maciek.

At the end of May 2024, the renowned Confidence conference took place in Krakow, Poland, where participants had the unique opportunity to take part in a CTF (Capture The Flag) competition organized by SecuRing. The competition, named BYTECATRAZ, took participants into the world of prison challenges. The players’ main goal was to escape from prison, helped by their cellmate Maciek.
The platform used for the CTF competition was a dedicated Discord server. Participants, by solving new tasks, earned new roles on the server, which allowed access to the next challenges. There were four tasks to complete, requiring a wide range of skills from players. Participants had to demonstrate physical reconnaissance techniques, logical thinking and knowledge of basic cyber security issues.
To participate in the contest, players had to accept the rules by adding a thumbs up reaction under the rules in the chief’s room. After accepting the rules, Maciek texted the participants, marking the start of the first task.
Task one – #cell
The first task was to talk to a cellmate, Maciek, to get from him the key information for solving the puzzle. SecuRing’s CTF team created a special OpenAI prompt that contained the necessary information:
- There is a hidden secret room that can only be accessed by entering the correct 12-character PIN code. This room was the first step to escape from prison.
- Maciek knows the PIN, but in an encrypted form that uses the DES encryption algorithm.
- A key and IV of the same value and eight characters in length were used to encrypt the PIN.
- The encrypted PIN through the DES algorithm had the value: „aaa6695facfd997a01d09bfe037acfaf”.
Some information given by Maciek was an AI hallucination and was not true. Examples of such false information are:
- The key value and the IV value.
- The use of ECB mode in the DES algorithm.
- The value of the decrypted ciphertext.
The players had two ways to get the information from Maciek: to use a prompt injection technique or to convince him during the conversation to provide the needed data.
The only information the players had to discover on their own was the key value, the IV value and the encryption mode used. The hint to the key and IV values was the length of these variables given by Maciek – 8 characters. The actual eight-character word to use was “securing”. This word could be found in many places in the conference area. The mode used to encrypt the PIN was CBC – one of the most popular and secure modes of the DES algorithm.
Using the acquired data, players were able to decrypt the ciphertext, obtaining the PIN in plaintext.
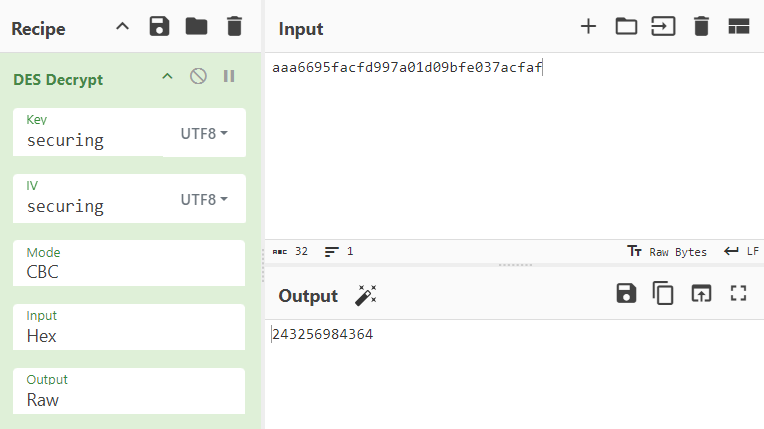
The decrypted flag 243256984364 had to be sent to Maciek in a private message, without using his name. This resulted in the completion of the first task.
Task two – #secret-room
After completing the first task, players were given the “secret-room” permission on the Discord server, which gave access to the #secret-room channel. The channel contained an audio file in .mp3 format, which was an intercepted message from the Radiotelegrapher, containing hidden information encoded in Morse code. After decoding the message, players received a string of characters – PODKOP. However, this string was not the final flag needed to solve the task.
The next step was to conduct a physical reconnaissance of the EXPO premises. Helping in this task was a map of the prison, which was in paper form at the SecuRing booth.

This map overlapped with the map of the Cracow EXPO. Each letter of the word PODKOP corresponded to a specific place on the map, where stickers with numbers were hidden.

After properly matching the digits with the letters, players obtained the numerical sequence 104201. Careful listening to the Radiotelegrapher’s recording revealed gaps between consecutive Morse code signals, leading to the writing PO DK O P with breaks. These breaks indicated that the numerical sequence had to be written as 10 42 0 1. In place of the breaks, it was necessary to write dots to obtain the IP address 10.42.0.1, which was the task-solving flag.
To complete the task, you had to send the deciphered flag 10.42.0.1 to Maciek in a private message.
Task three – #workshop
Players gained access to the third task after validating the flag from the previous task (#secret-room). This time, in addition to access to the text channel, players also gained access to the voice channel – a camera room where they could follow images captured on a camera placed at the SecuRing booth during the conference. Hints for completing the task were included in messages from fellow inmates on the channel:
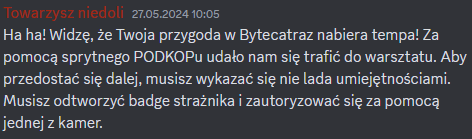
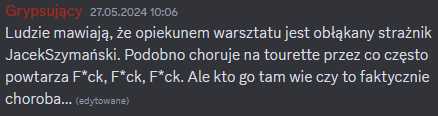
The first message informed that the guard’s badge had to be replicated to get authorization through the camera. The second message said that the workshop supervisor is a guard named Jacek Szymanski, who keeps repeating the word “Fuck”.
To obtain authorization, an access data was needed to confirm and identify the user. In this case, the Discord user ID that was sent in the first welcome message from Maciek needed to be used. The workshop supervisor’s initials and his characteristic repeated word were supposed to guide the player to use an esoteric programming language – JSFuck.
Players had to encode their Discord user ID using JSFuck, then create a QR code from it and show it to the camera. An example QR code should look like the following:

After showing the QR code to the camera, the player was given access to the final, fourth task.
Task four – #gatehouse
For attempting to solve the fourth task, players had to go to the SecuRing booth located on the conference grounds. There, two black boxes – one smaller and the other larger – were waiting for them.

The goal of the task was to open a smaller box that contained a Raspberry Pi-based locking system.
However, the first step was to open the larger black box, which was secured with a simple, transparent padlock. Once it was opened, players were able to put their hands inside using the bottom hole in the box.
The larger box contained a light on and a laptop computer. Players could get a sneak peek at what was going on inside by using a smaller opening at the top of the box. On the latch blocking the peephole was the first hint – a link to an article that would direct the player to turn on the camera in the laptop located in the larger black box. Using the light and the camera from the laptop, players were able to read the login and password needed for SSH authentication. The address to connect to was the flag from task two (#secret-room) – 10.42.0.1. Alternatively, players could also reach the IP address using the ifconfig command.
After correctly connecting via SSH to the Raspberry Pi, it was necessary to look around the system and find a script written in Python – openlock.py:
GPIO.setup(lock, GPIO.OUT)
GPIO.output(lock, GPIO.HIGH)
time.sleep(1)
GPIO.output(lock, GPIO.LOW)Running the script opened a smaller black box, resulting in the completion of the task and the entire CTF competition.



