Threat-Led Penetration Testing (TLPT) – How to be DORA compliant in 2025?
The Digital Operational Resilience Act (DORA), coming into effect in January 2025, imposes new cyber-resilience obligations on financial institutions in the European Union.

Table of contents
- What does DORA mean for financial institutions?
- What are the TLPT tests and why are they crucial for DORA?
- Why was Threat-Led Penetration Testing (TLPT) introduced?
- What is DORA?
- DORA key areas of regulation
- What are Threat-Led Penetration Tests (TLPT)?
- What makes TLPT differ from traditional penetration testing?
- Key elements of Threat-Led Penetration Testing (TLPT)
- Implementation stages of Threat-Led Penetration Testing (TLPT)
- DORA requirements regarding Threat-Led Penetration Testing (TLPT)
- ICT Risk Management and the Role of Threat-Led Penetration Testing (TLPT)
- Why choose Securing to implement Threat-Led Penetration Testing (TLPT)?
- (FAQ) Frequently Asked Questions – Threat-Led Penetration Testing (TLPT)
What does DORA mean for financial institutions?
The Digital Operational Resilience Act (DORA), coming into effect in January 2025, imposes new cyber-resilience obligations on financial institutions in the European Union. It aims to increase the operational security of the financial sector by introducing standards for IT risk management. One of the key requirements of DORA is the implementation of Threat-Led Penetration Testing (TLPT), which is designed to test how well your organization handles real-world cyber threats.
TLPT testing is particularly important for banks, insurance companies, fintechs and other supervised entities, such as those regulated by financial regulatory authorities. Meeting DORA requirements means not only compliance with regulations, but also a real strengthening of your organization’s operational security.
Get in touch with the specialist on LinkedIn!

What are the TLPT tests and why are they crucial for DORA?
Threat-Led Penetration Testing (TLPT) is advanced security testing that combines analysis of current threats (Threat Intelligence) with simulations of actual attacks (Red Teaming). They focus on the most critical assets and business processes to comprehensively assess an organization’s ability to detect and respond to cyber attacks.
TLPT testing integrates three key elements:
- Threat Intelligence – analysis of current threats,
- Red Teaming – simulating the activities of cybercriminals,
- Resilience Assessment – examining how an organization detects and responds to cyber attacks.
Why was Threat-Led Penetration Testing (TLPT) introduced?
Recent years have seen a rapid increase in the number of cyberattacks targeting the financial sector. DORA was created as a response to these threats, providing financial institutions with a legal framework and tools to build resilience. TLPT is a practical component of this framework that allows organizations to not only meet regulatory requirements, but also to protect their reputations and finances from the effects of cyber attacks.

What is DORA?
The DORA directive is designed to:
- Reduce the risk of operational disruption caused by cyberattacks.
- Create a uniform standard for digital resilience in the financial sector across the EU.
- Increase financial institutions’ responsibility for IT risk management.
DORA key areas of regulation
- ICT risk management: organizations must implement systems to manage information and communications technology risks.
- Incident reporting: all ICT security incidents must be recorded and reported to regulators.
- Digital resilience tests: financial institutions must conduct tests, including TLPT tests.
- ICT provider management: full control over the risks associated with external services is required.
- Cooperation and information sharing: promoting cooperation between institutions in the field of cybersecurity.
What are Threat-Led Penetration Tests (TLPT)?
TLPT is penetration testing that focuses on simulating real-world attacks. The purpose of TLPT is to assess:
- Resilience of the organization to cyber threats.
- Effectiveness of defense mechanisms.
- Readiness of security teams.
In short, TLPT tests are comprehensive tests that examine:
- Technology – the effectiveness of security systems,
- People – the awareness of employees and their response to threats,
- Procedures – the effectiveness of incident response.
What makes TLPT differ from traditional penetration testing?
- Threat-Led Penetration Testing (TLPT) is based on actual threat data (Threat Intelligence).
- Threat-Led Penetration Testing (TLPT) uses Red Teaming techniques that simulate real threats on production systems.
Traditional penetration tests (pentests) focus on identifying technical vulnerabilities in systems and applications through a detailed analysis of their security. They are typically extensive but focus on vulnerabilities – their goal is to find security gaps that can be fixed before they are exploited by attackers.
Threat-Led Penetration Testing (TLPT), on the other hand, goes a step further. Based on Threat Intelligence, TLPT focuses on simulating the activities of advanced attack groups (APTs), using realistic scenarios based on real-world threats and attack techniques. TLPT tests focus on assessing the overall resilience of an organization, including the effectiveness of detection systems, response teams and defense procedures – which goes beyond traditional technical vulnerability testing.
Key elements of Threat-Led Penetration Testing (TLPT)
1. Threat Intelligence:
- Analysis of current cyber threats affecting the tested organization.
- Use of information about hacker groups, attack techniques, and known vulnerabilities.
What is Threat Intelligence?
Threat Intelligence (TI) is the process of collecting, analyzing and using cyber threat data to understand, predict and prevent attacks on an organization. In the context of Threat-Led Penetration Testing (TLPT), Threat Intelligence is an essential component because it provides the basic information for creating realistic test scenarios and ensures that the tests reflect the actual threats an organization may face.
Key elements of Threat Intelligence in Threat-Led Penetration Testing (TLPT)
1. Collecting threat data:
This data comes from various sources, such as:
- Public databases of vulnerabilities (e.g., CVE – Common Vulnerabilities and Exposures),
- Security incident reports,
- Information from Threat Intelligence vendors.
- Dark web and cybersecurity forums.
2. Threat analysis:
Data is processed to understand:
- Tactics, techniques and procedures (TTP) used by attackers,
- Attack vectors and their potential impact on the organization,
- Trends in cybercrime activities (e.g., increase in ransomware attacks).
3. Data contextualization:
Threat Intelligence must be tailored to the specifics of the organization. Examples:
- Which APT groups might be interested in the financial industry?
- Which organization’s systems are most vulnerable to attacks?
- What data is most valuable to potential attackers?
4. Transforming data into action:
Based on the collected and analyzed information, the following is created:
- Realistic attack scenarios in TLPT tests,
- A list of the most critical vulnerabilities to be checked,
- Recommendations for security enhancements.
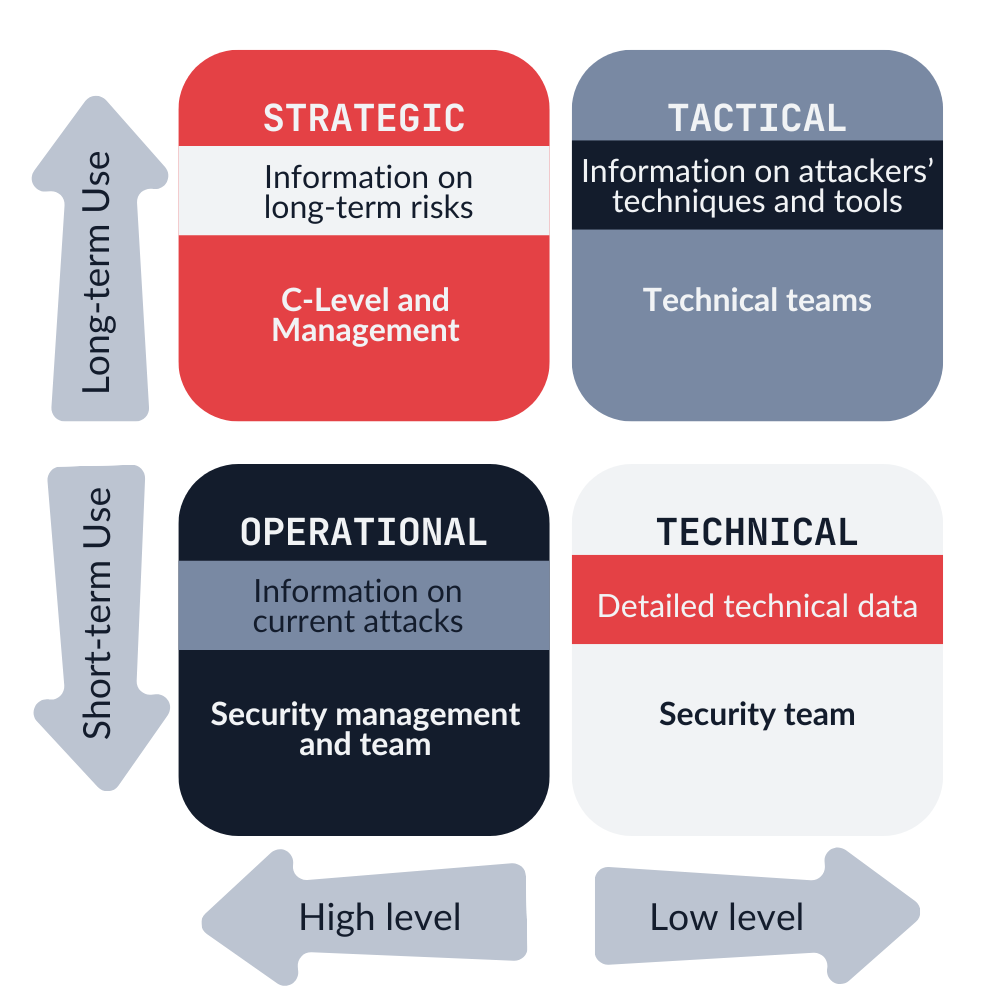
Types of Threat Intelligence in Threat-Led Penetration Testing (TLPT)
1. Strategical Threat Intelligence:
- Information on long-term threats, such as APT groups targeted against the financial sector.
- Helps management and security leaders understand potential risks and make decisions about security investments.
2. Tactical Threat Intelligence:
- Data on specific techniques and tools used by cybercriminals.
- Useful for technical teams to adjust security measures.
3. Operational Threat Intelligence:
- Information about current threats, such as malware activity or phishing targeted against the organization.
- Used in real time to respond to threats.
4. Technical Threat Intelligence:
- Detailed technical data such as IP addresses, domains, and malware signatures.
- Useful for network monitoring and incident response.
2. Red Teaming:
- Tests that simulate advanced attacks designed to compromise the organization’s security.
- They test the organization’s ability to detect and respond appropriately to an incident.
What is Red Teaming in the context of Threat-Led Penetration Testing (TLPT)?
Red Teaming is an advanced security testing methodology that simulates the actions of people – such as cybercriminal groups or advanced attack groups (APTs) – to assess the overall resilience of an organization to threats. Although often associated with physical testing, such as attempts at unauthorized access to buildings or physical security, Red Teaming covers a much broader scope and is applicable in many different areas.
What does Red Teaming cover?
1. Technical tests:
- Attempts to breach IT systems, applications, and network infrastructure.
- Use of techniques such as phishing, brute force or exploitation of system vulnerabilities.
2. Physical tests:
- Attempts to physically access facilities, such as impersonating employees, breaking entry security, or using fake IDs.
3. Social engineering tests:
- Manipulating employees to gain access to systems or information (e.g., phishing, vishing or personal interactions).
4. Evaluation of processes and reactions:
- Testing the effectiveness of incident response procedures.
- Testing how IT and operational security teams detect and respond to incidents.
Why is Red Teaming essential in Threat-Led Penetration Testing (TLPT)?
Unlike traditional penetration testing, which focuses on identifying technical vulnerabilities, Red Teaming assesses the ability of the entire organization to defend against threats. This includes:
- Testing people: Are employees aware of threats and do they follow security procedures?
- Testing technology: Do systems detect attacks and block them appropriately?
- Testing processes: How effectively do incident response and escalation mechanisms work?
Red Teaming in TLPT allows organizations to look at their security from the attacker’s perspective, identifying not only technical vulnerabilities, but also weaknesses in procedures and employee awareness. This allows organizations to prepare more effectively for real threats.
Implementation stages of Threat-Led Penetration Testing (TLPT)
1. Planning:
- Defining the objectives of the test.
- Determining the scope, including critical systems and processes.
2. Preparation:
- Collecting data about the organization.
- Developing test scenarios based on Threat Intelligence.
3. Implementation:
- Simulating attacks according to established scenarios.
- Testing the effectiveness of detection and response systems.
4. Reporting:
- Analyzing test results.
- Providing recommendations for security improvements.
5. Removing vulnerabilities and verifying fixes:
- Implementing the recommendations.
- Re-testing to verify the effectiveness of the changes made.
DORA requirements regarding Threat-Led Penetration Testing (TLPT)
According to DORA:
- Threat-Led Penetration Testing (TLPT) must be conducted by independent and market-recognized vendors with appropriate qualifications (e.g., OSCP, CREST certifications).
- Testing must be conducted at least once every 3 years. Competent authorities may reduce or increase this frequency for an entity, depending on its risk profile or operational circumstances.
- The results of Threat-Led Penetration Testing (TLPT) must be documented and reported to the relevant supervisory authorities.
ICT Risk Management and the Role of Threat-Led Penetration Testing (TLPT)
TLPT is a key tool in ICT risk management because:
- They enable the identification and elimination of critical vulnerabilities.
- They provide an organization with full insight into its ability to counter threats.
- Are the foundation for building a risk management strategy in accordance with DORA.
Why choose Securing to implement Threat-Led Penetration Testing (TLPT)?
When selecting a partner to implement Threat-Led Penetration Testing (TLPT), experience, competence and the ability to meet regulatory requirements, such as those imposed by DORA, are critical. At Securing, for more than 20 years we have been providing comprehensive cyber security solutions to the financial sector and other industries requiring the highest standards of protection.
Our experience
- More than 20 years on the market: For more than two decades, we have been supporting organizations in protection against cyber threats. Our solutions are tailored to rapidly changing legal and technical requirements.
- Hundreds of clients in the financial sector: We have worked with banks, insurers, fintechs, and other financial institutions around the world. Our projects have included both local and global entities.
- Cooperation with financial authorities: Having worked with regulators and regulatory institutions, we understand the specifics of requirements such as DORA or guidelines from local regulators.

Expertise and competence
- Team of experts: At Securing, we permanently employ dozens of experienced pentesters who specialize in advanced and diverse security testing.
- Certifications and standards: Our specialists hold the most important industry certifications, including CREST, OSCP, CEH, which are required in the context of TLPT implementation in accordance with DORA and TIBER-EU regulations.
Why organizations choose Securing
- Personalized approach: We customize our activities to the specifics of each client’s business, taking into account their unique needs and priorities.
- Minimal involvement of your IT department: Our experts will conduct TLPT tests without overburdening your team.
- DORA compliance: We ensure that the tests performed comply with regulatory requirements and local regulators’ guidelines.
- Real results: Our recommendations have helped thousands of organizations improve their security levels and reduce operational risks.
- Comprehensive support: We offer support at every stage of TLPT – from planning through implementation to remediation and retesting.
Thanks to DORA and mandatory TLPT tests, the financial sector is becoming more resilient to cyber threats. Implementing these tests is not only a regulatory requirement, but also an investment in operational security, protecting customer data and building trust in the market.
Contact us and we will provide your organization with comprehensive support, regulatory compliance and top-quality security.
(FAQ) Frequently Asked Questions – Threat-Led Penetration Testing (TLPT)
FAQ – table of contents
- What is Threat-Led Penetration Testing (TLPT)?
- Why are TLPT tests important in the context of DORA?
- What companies must conduct TLPT testing?
- How long does it take to implement Threat-Led Penetration Testing (TLPT)?
- What is Red Teaming and why is it important?
- What is the role of Threat Intelligence in TLPT testing?
- Can TLPT tests be conducted by internal IT teams?
- What are the requirements for teams conducting Threat-Led Penetration Testing (TLPT)?
- Is Threat-Led Penetration Testing (TLPT) mandatory for small financial institutions?
- What does the Threat-Led Penetration Testing (TLPT) report include?
- How often should Threat-Led Penetration Testing (TLPT) be conducted?
- What happens if an organization does not conduct Threat-Led Penetration Testing (TLPT)?
- Can Threat-Led Penetration Testing (TLPT) detect all vulnerabilities in IT systems?
- What are the main differences between TLPT testing and standard penetration testing?
- Red Teaming as a methodology
- Can Threat-Led Penetration Testing (TLPT) cover IT vendors?
- How to prepare an organization for TLPT testing?
- Does Securing offer support after TLPT testing?
- Is Threat Modeling the same thing as Threat Intelligence?
1. What is Threat-Led Penetration Testing (TLPT)?
Threat-Led Penetration Testing (TLPT) is an advanced form of penetration testing that simulates real-world cyber threats to test an organization’s resilience. It uses scenarios based on Threat Intelligence data and Red Teaming techniques.
Important: Threat-Led Penetration Testing (TLPT) consists of Threat Intelligence and Red Teaming phases, carried out by separate, specialized teams.
2. Why are TLPT tests important in the context of DORA?
DORA requires the implementation of Threat-Led Penetration Testing (TLPT) as a tool for assessing cyber resilience. This is a key compliance criterion required by EU and local regulations.
3. What companies must conduct TLPT testing?
TLPT tests are mandatory for:
- Banks,
- Insurers,
- Investment companies,
- Fintechs,
- IT service providers supporting financial institutions.
4. How long does it take to implement Threat-Led Penetration Testing (TLPT)?
The TLPT testing process usually takes 3-4 months. The duration depends on:
- Size of an organization,
- The complexity of IT systems,
- The scope of testing and the number of scenarios.
5. What is Red Teaming and why is it important?
Red Teaming is a method for simulating the actions of real-world attackers. It combines technology with social engineering and physical attacks to assess the organization’s security.
6. What is the role of Threat Intelligence in TLPT testing?
Threat Intelligence provides data on:
- Current threats,
- Technologies and tools used by cybercriminals,
- Vulnerabilities in IT systems.
7. Can TLPT tests be conducted by internal IT teams?
Yes, DORA (Digital Operational Resilience Act) allows the use of internal IT teams to conduct TLPT (Threat-Led Penetration Testing), but under certain conditions:
- Approval of relevant authorities: The use of internal testers must be approved by the relevant supervisory authority or designated public entity.
- Verification of resources: The supervisory authority must confirm that the financial institution has sufficient resources dedicated to testing and that it avoids conflicts of interest in designing and implementing the tests.
- Third-party Threat Intelligence provider: the Threat Intelligence provider must be external to the financial institution.
8. What are the requirements for teams conducting Threat-Led Penetration Testing (TLPT)?
Teams conducting TLPT tests must, among other things:
- Have certifications (e.g., OSCP, CEH, CREST),
- Have experience in Red Teaming,
- Use an ethical and professional approach.
The full list of requirements is available at the link.
9. Is Threat-Led Penetration Testing (TLPT) mandatory for small financial institutions?
Yes, DORA covers all financial institutions, regardless of their size, if they are covered by EU regulations.
10. What does the Threat-Led Penetration Testing (TLPT) report include?
The TLPT report includes:
- Test results,
- A list of identified vulnerabilities,
- Analysis of the security mechanisms’ effectiveness,
- Recommendations for improvements.
11. How often should Threat-Led Penetration Testing (TLPT) be conducted?
DORA requires TLPT to be conducted at least once every three years. However, organizations can increase the frequency depending on internal recommendations from safety departments. Additionally, regulators may require more frequent testing if they consider it necessary.
12. What happens if an organization does not conduct Threat-Led Penetration Testing (TLPT)?
Failure to implement Threat-Led Penetration Testing (TLPT) may result in:
- Financial penalties,
- Regulatory compliance violations,
- Increased risk of cyber attacks.
13. Can Threat-Led Penetration Testing (TLPT) detect all vulnerabilities in IT systems?
TLPT tests focus on critical vulnerabilities and realistic attack scenarios. They are not a substitute for regular penetration testing, but rather a complement to it.
14. What are the main differences between TLPT testing and standard penetration testing?
- TLPT testing: Realistic scenarios, Threat Intelligence data, Red Teaming.
- Standard Penetration Testing: Broader scope but less detailed approach to realistic threats.
15. Red Teaming as a methodology
Red Teaming is not just a set of tools or activities – it’s a methodology that integrates different types of testing (technical, physical, socio-technical) into one cohesive process. As a result:
- Test scenarios are comprehensive and reflect real threats.
- Tests can be tailored to the specifics of the organization and its critical assets.
- The test results provide valuable information on real-world resilience to threats.
Myth: Red Teaming is just physical testing
One of the most common misunderstandings is the belief that Red Teaming is limited to physical tests, such as breaking the security of buildings. In fact, physical testing is only one part of the methodology. Red Teaming includes:
- Technical tests of IT infrastructure.
- Attempts to manipulate people (social engineering).
- Verification of incident response procedures.
16. Can Threat-Led Penetration Testing (TLPT) cover IT vendors?
Yes, according to DORA, TLPT testing can also cover IT service providers if their systems are critical to the operation of the financial organization.
17. How to prepare an organization for TLPT testing?
- Identify key systems and processes,
- Ensure management support,
- Select a trusted vendor with experience in TLPT implementation.
18. Does Securing offer support after TLPT testing?
Yes, Securing not only performs Threat-Led Penetration Testing (TLPT), but also:
- Supports implementation of recommendations,
- Offers training to IT teams and management,
- Performs retests to verify implemented patches.
- Offers a full range of services and training in the broad field of cyber security.
19. Is Threat Modeling the same thing as Threat Intelligence?
No, Threat Modeling (TM) and Threat Intelligence (TI) are two different things.
- Threat Modeling identifies threats in a system.
- Threat Intelligence collects data on current threats.
Get in touch with the specialist on LinkedIn!




