Why is it good to look back at your older iOS application builds?
This article shows why you should always change the secrets in case they were leaked in previous versions of the application.

Some may be wondering: “what happens to the leaked secrets? You’ve pushed a new build without compromised secrets, so you think you are secure now, don’t you?
Well, not exactly. Here’s why:
Getting IPA Files in order to look for leaked secrets
Speaking about iOS, the main application distribution (and redistribution) point is AppStore. Applications placed there can be downloaded on iPhone or straight to macOS for analysis, utilizing tools like Apple Configurator 2.
IPA (iOS AppStore Package) is a simple structured signed zip file, which contains all the necessary files that will be further unpacked on the device. Additionally, Apple makes sure that applications binary redistributed by AppStore are always encrypted, so the attacker cannot easily reverse-engineer the application source code.
In order to look for secrets, the attacker may choose one of two paths:
Download the IPA file straight to their PC and analyze its content.
This is a rather simple approach. The attacker can do it manually or with tools that will search for particular regular expressions. Automatic scans may find some false positives, but often allow for scanning many targets at once.
In order to do that, simply install an application on your iPhone, connect the iPhone to the macOS and start Apple Configurator. Choose Add -> Apps and wait for the warning to appear:
If the warning appears, it’s all good. The IPA File can be found at:
~/Library/Group Containers/K36BKF7T3D.group.com.apple.configurator/Library/Caches/Assets/TemporaryItems/MobileApps/The second option is to download IPA to the jailbroken iOS device and decrypt the binary file.
This can be done with Frida, which provides an easy way to decrypt and transfer files to the macOS for further analysis. This approach takes slightly more time, but gives the attacker the ability to look inside the binary. If any password or secret are hardcoded inside, then it would not be visible while using the first approach.
If your device is jailbroken, you can decrypt binary and dump IPA file with iOS Frida Dump.
What can go wrong?
What are the chances that the current version of the application contains secrets?
Rather Small.
What are the chances that there were some secrets included in previous builds?
Slightly bigger.
Once published, the Application Package does not disappear from the store. This can be used by the attacker to download previous builds of the application and analyze them as well. By intercepting HTTPS transmission on iOS device, the attacker may list all available previous builds by viewing response from the following endpoint:
p35-buy.itunes.apple.com/WebObjects/MZBuy.woa/wa/buyProduct?guid= The response contains an XML file and all versions possible to download can be found under softwareVersionExternalIdentifiers key. The request is triggered after pressing the redownload button in the AppStore.
Example of the response:
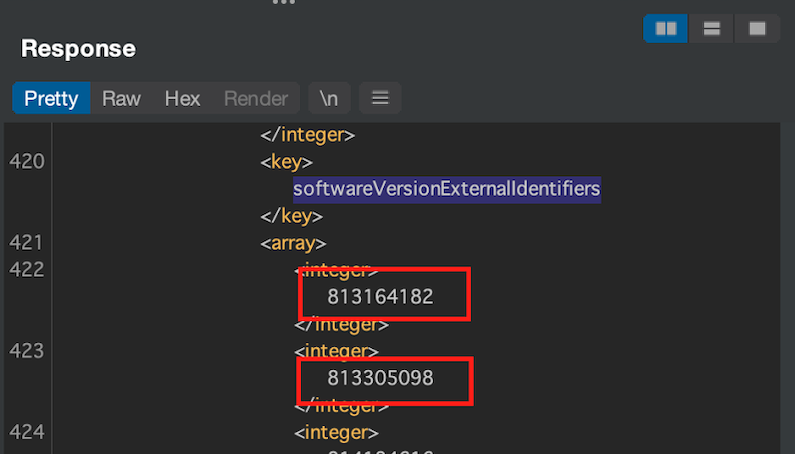
After cancelling the download and modifying the request by adding &appExtVrsId=putVersionIdentifierHere to the querry string – the old version of the application will be downloaded.
This way it is possible to download a deprecated version of the application to the device and later, the app can be dumped using Frida. Even if the current build is secrets-free, it is not guaranteed that those secrets won’t be found in previous ones.
What should I do if secrets were pushed to the final build?
If you find out that the secrets were pushed to the final build, it is recommended to push a new build as soon as possible and rotate the leaked keys to minimize the impact.
How to handle old versions of the apps?
Leaks happen, so it is really important to clean up the mess. Every time you push a new build to the AppStore, you should remember to change any secret or password that could have been obtained by potential attackers. As shown above, it is relatively easy to obtain the old versions, so keep in mind that secrets, once leaked, should always be treated as compromised.
If you want to know more about good practices of iOS application development, we’ve put up a guide that compiles our iOS security knowledge into one piece:




